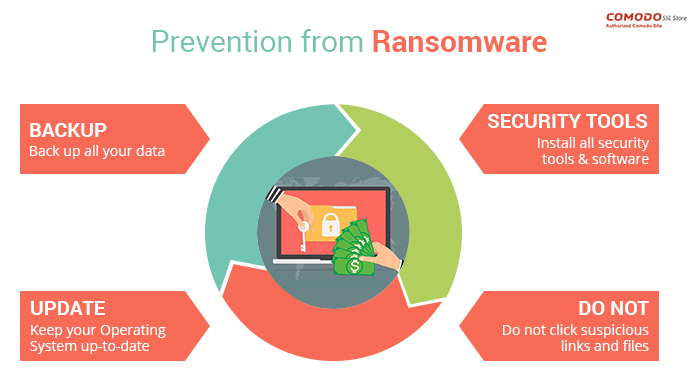
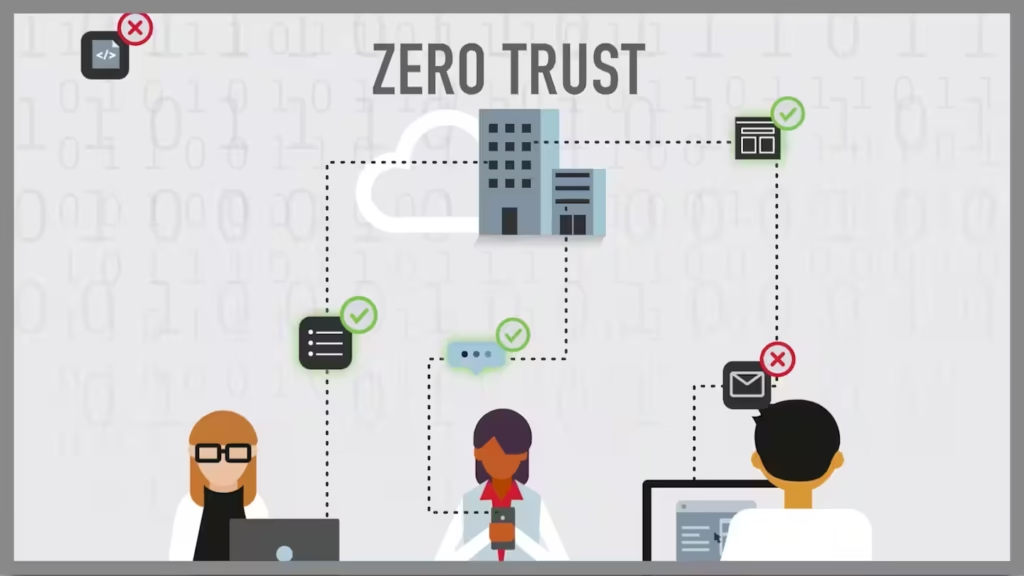
Incident Response Plans: Preparing for Cybersecurity Breaches and Attacks
Incident Response Plans: Preparing for Cybersecurity Breaches and Attacks In an era where cyber threats are increasingly sophisticated and prevalent, organizations must prioritize their cybersecurity posture. One of the most effective ways to mitigate the impact of a breach or attack is through a well-defined Incident Response Plan (IRP). An IRP provides a structured approach […]